
ARESx
You want a battle?
We'll give you a war.
NEW SITE IS UNDER CONSTRUCTION
Upcoming CTFs Timer
Fword CTF

ALLES! CTF 2020

The Team

Main Team
Team Captain:
MillenniumX - Greetings! You can call me MillenniumX, and I'm a high school student. I do bug bounty hunting, iOS development, astronomy and writing (mainly plays and poetry). I'm currently into web exploitation, but starting to learn a little about reverse engineering. I love CTFs due to their competitive yet friendly spirit, and in my free time you can find me listening to NF, Witt Lowry and Vobah!
Members:
1. Gh0stPepper - Hi! I'm Gh0stPepper, and I'm a student. I love cryptography and stenography, as well as web hacking, and am always learning.
Outside of CTFs, I love alternate reality games, Animal Crossing, and listening to music, especially Taylor Swift and The 1975.
2. wotwot - I'm a software development student who focuses on Cyber security, my main area of expertise lie with binary reverse engineering and exploiting & web exploiting. I enjoy doing CTF's & HTB.
3. LEVI - Hi there! My name's Levi. I'm a high school student and an ethical hacker that aims to be a greater hacker and secure the World Wide Web. Besides from hacking, I like gaming, programming, robotics, physics etc. I'm not that much of a talk guy, but I understand people and give them support whenever they need me!
4. Teak - Teak is a professional AppSec specialist with many CTFs and HTBs under his belt, currently looking to get into Bug Bounties. His expertise is in reversing, ROP, and web apps, but he's always looking to learn more, and hone his hackingness. He's always happy to teach to any level of understanding, so don't be afraid to ask any questions.
5. spitfire - Hello! I'm spitfire. I am an informatics (arguably compsci, idk my college's curriculum is confusing) undergrad student, and really interested in being a security analyst. I can do forensics thingy like memory forensics, packet forensics, storage forensics, and understand Cisco network security. I do CTFs for about a year now, and in the meantime I'm a Python developer. Please guide me to the wonderful world of pentesting! I'm also an electronic music producer, mainly drum and bass, so hit me up if you need a keygen music :d
6. tsk - Hello! I am tsk. I am an Application Security Engineer by trade. I build out enterprise level appsec programs for companies. I have experience as a full-stack developer, leading appsec teams, consulting for multi-nationals, and I like to hack on the side for fun when I can. I like going to live hacking competitions with my friends and competing in online CTFs too! I have a B.S. in Computing Security and a passion for learning. My experience is in malware reverse engineering, tons of programming languages, web security, penetration testing, linux systems, and much more!
7. 520 - I'm a penetration tester for a major UK firm, and I'm the kind of person that loves solving puzzles. When I'm not hacking, I'm trying to put my Python knowledge to good monetary use.
8. Xiahou - Hey! I'm Xiahou, a high school student who picked up cybersecurity as an interest and intend to make a life out of in the future. I consider myself a jack of all trades but master of none when it comes to challenges, and strive to become better quickly.
9. Oceans - Hello, I'm Oceans, currently working in the IT field for the DOD looking to expand my knowledge and experience in the red team field. I currently specialize in steganalysis/forensics as well as powershell scripting and python programming. Currently rocking SEC+, CCNA, CIW, SEO, and A+ certifications and looking to go for my CYSA and CISSP. I'm a huge fan of playing CTF events and learning all that I can from the community.
10. R3N4SCITUR - I'm R3N4SCITUR and I'm here to learn from like minded people and have fun doing it. I have always been passionate about technology. I'm obtaining a BA in IT w/emphasis on cyber security. I enjoy CTFs because they are an almost impossible puzzle at first but as you take the time to break them down, you realize there is a solution.
11. noobs3c - My name is Sofiane (aka noobs3c) and I'm a 19 year old French/Morrocan security researcher and bug hunter who lives in France. Currently, I'm a first year student in IT engineering and I hope to work in cybersecurity in the future! I'm practicing really frequently and really hard by playing multiple CTFs. I love to share resources with others!

Subsidiary Team
Team Captain:
Wisty
Members:
1. dropcake
2. TedZak
3. SCAND1UM
4. m1rz
5. Indura
6. MrEvil
7. h@shbr0wn
8. Severe
9. QTheBear
10. ElementalX
11. wej ynit
Contact Us
Hi! If you would like to contact ARESx, either go to our Discord server, or email us directly! Follow us on Twitter for updates!
Writeups
PoseidonCTF
Gallery - wej ynit
PoseidonCTF
Statement:
i have an old damaged disk , it contains a lot of my images , i use it as a gallery actually , in it , i had a secret can you get it back for me ?
Solution:
1. The file that was attached was .E01 disk image I opened the disk image using Autopsy and extracted everything i thought looked interesting (2 txt files and bunch of images)
2. One of the two txt files was called 121-steghide.txt, alluding that steghide was used to hide the message and second was called 123-Garbage.txt which looked like random strings, yet i thought could be useful later on.
3. Using steghide info <filename> to check every JPG image for possible hidden message, excluding PNG since steghide works only on JPG, BMP, WAV and AU
4. Only JPG image that reacted to steghide info was called 95-WallpaperHD19756487Ef4.jpg and asked for password which I didn't have
5. After searching for password in autopsy, i thought 123-Garbage.txt had a purpose and for some reason every string inside it was same length.
6. I used 123-Garbage.txt now as a wordlist for a password bruteforcing a way in, leaving me a text file 95-WallpaperHD19756487Ef4.jpg.out containing message that was hidden int the image - “the flag”
FLAG: Poseidon{uR34G00D_AN4Ly5t}
sh*tty ransomware - Oceans
PoseidonCTF
A write up regarding the Forensics challenge Shtty Ransomware
So the challenge tells us about a peice of malware that infected someones computer
disguised as a game and we're asked to find the IP and PORT number associated with it
To begin we start off by downloading a file called
ShttyRansomware.raw
A simple strings search of the file shows a ton of info regarding a windows machine
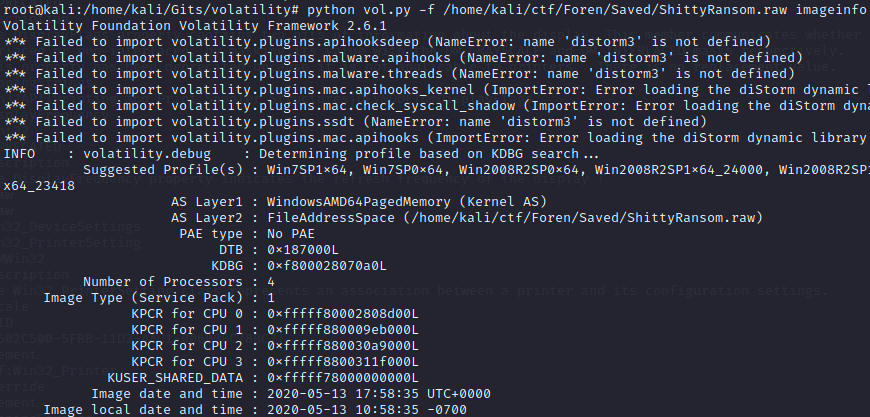
Lets trying running Volatility on it to see if we're playing with a Dump file.
python vol.py -f ShittyRansomware.raw imageinfo
Sure enough! Now we can extract some data
Now lets look at web history of this user
I'm using the plugin - Chromehistory from 'superponible'
python vol.py -f ShittyRansomware.raw --profile=Win7SP1x64 chromehistory
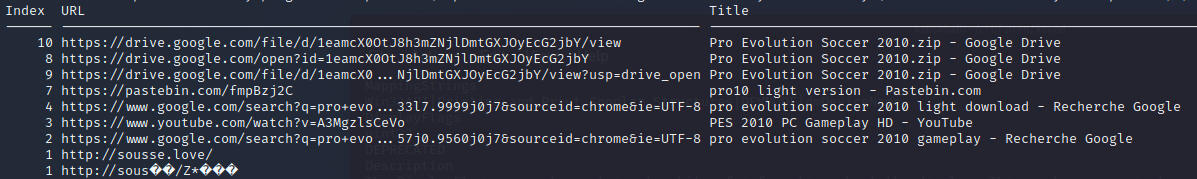
Here we can see 2 interesting links
Google Drive - Pro Evolution Soccer Pastebins - pro10 light version
If we take a look at the pastebins file we see some interesting info
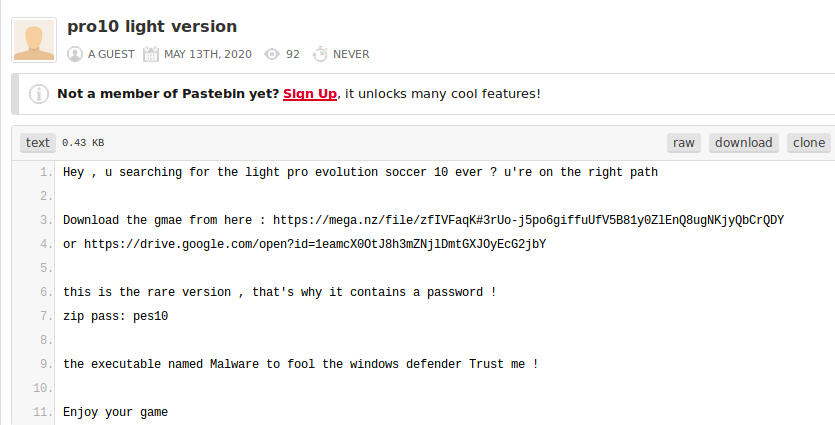
A link to the game and a password for the file
After downloading and extracting the files we now have the malware executable
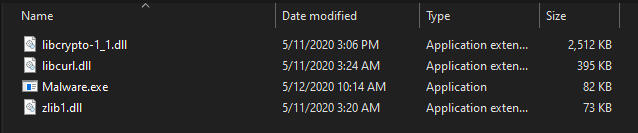
Now we need to see where its pointing...
Lets load up wireshark and capture the packets while running the malware.
We can see an HTTP GET request was made
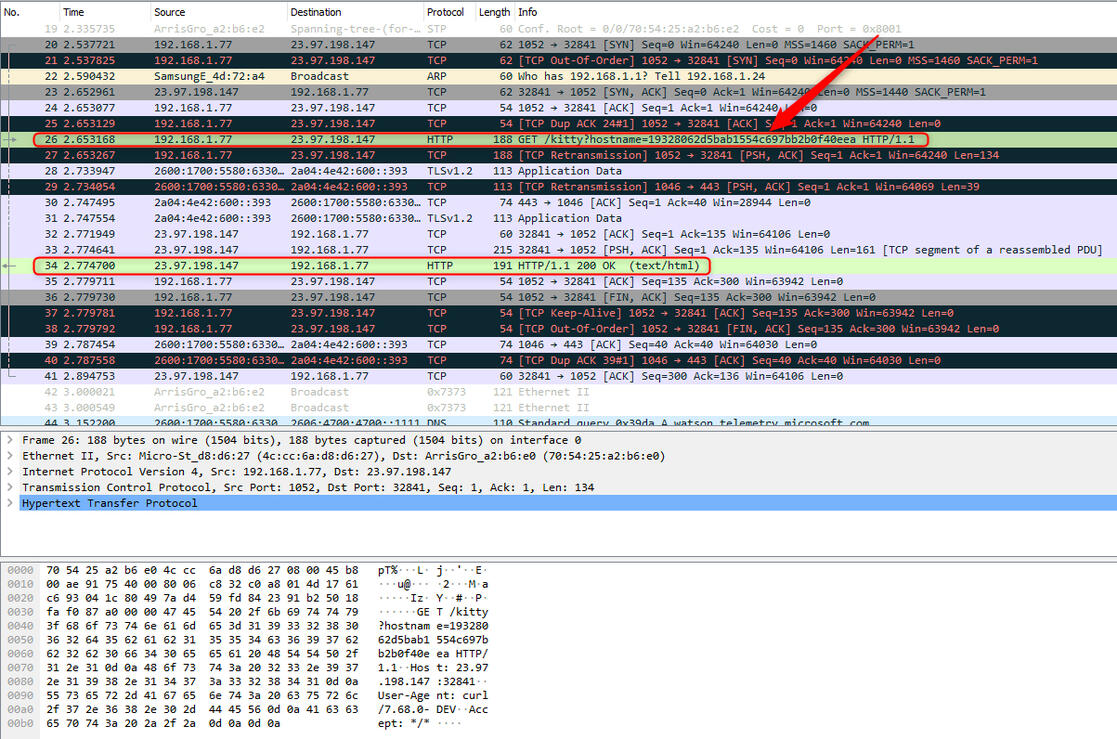
If we follow the HTTP stream we can now see the IP and PORT the malware was trying to contact
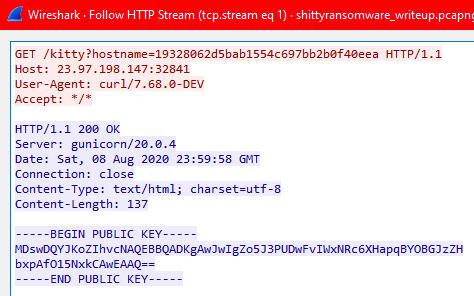
Now if we follow the IP and PORT
http://23.97.198.147:32841
It will return the flag

FLAG: Poseidon{HUhu'R3G0OD4tD1gG1nG}

